How can developers securely provision and onboard thousands of STM32 IoT devices to a cloud service? The answer may be QuarkLink™, a solution by Crypto Quantique, a member of the ST Partner Program that facilitates key management, automates onboarding procedures, and provides a dashboard to manage devices remotely. The solution works with STM32 microcontrollers or the STSAFE-A110 secure element. The company also provides a trial version running on the B-L4S5I-IOT01A Discovery kit and connecting to AWS. Developers can thus rapidly test QuarkLink’s APIs and services. The solution also supports Microsoft Azure, Eclipse Mosquitto, and can even fit unique cloud computing platforms.

QuarLink, security in IoT is much more than cryptography
Why do developers need more than simply cryptographic tools?

Crypto Quantique made a name for itself with its Quantum Driven Identity (QDID), a hardware root of trust that uses foundational notions in quantum mechanics to create seeds and identities that can’t be forged. The company then released QuarkLink to help customers automate provisioning and onboarding operations. Indeed, the company realized that too many teams releasing IoT systems need secure systems and a way to deploy and manage them. Strengthened by the success of its solution, Crypto Quantique realized QuarkLink could reach far more applications by targeting systems using something other than its QDID, such as those with a secure element like the STSAFE-A110 or an STM32.
Why do developers think of starting from scratch?
The challenge is that teams may sometimes be reluctant to adopt a third-party solution and prefer to write everything from scratch. There’s always a fear that another company owns the certificate or that developers must adopt a platform or system they may not be familiar with, thus creating new barriers to adoption. Many decision-makers also worry that such a solution will increase their data needs significantly, thus driving costs upward. Finally, some underestimate the industry requirements and technical expertise needed to deploy secure solutions on a large scale. Hence, as Crypto Quantique aimed to democratize security on STM32, it brought answers to all these challenges.
ST Partner Program and Crypto Quantique, empowering teams takes a whole ecosystem
How to prioritize accessibility and efficiency?
To ensure that more customers can quickly adopt QuarkLink, Crypto Quantique made the server interface agnostic, meaning that it takes the form of a Docker container that runs on nearly any operating system. The application requires a minimum of two cores and 8 GB of RAM. Additionally, QuarkLink keeps costs low by mainly using data during onboarding. Developers then decide how often they want their IoT devices pinging the server. In most scenarios, edge systems need very little data. For instance, if a device is no longer authorized to access the cloud, QuarkLink works on the cloud infrastructure to prevent that device from connecting. It’s also possible to use a machine-to-machine system to revoke certificates.
How to create a powerful ecosystem?

The system’s ability to run on STM32 or STSAFE devices and the trial version for our Discovery kit is highly symbolic because it testifies to the close partnership between ST and Crypto Quantique. The latter will also support the STM32U5 to take advantage of its TrustZone feature. QuarkLink thus shows what teams working on the STM32 ecosystem can expect from the ST Partner Program. Indeed, QuarkLink on STM32 is a comprehensive approach that provides everything needed to link a device to a cloud platform. Developers can also access a command-line interface to run a headless system or use scripts to automate operations.
How to get started with QuarkLink?
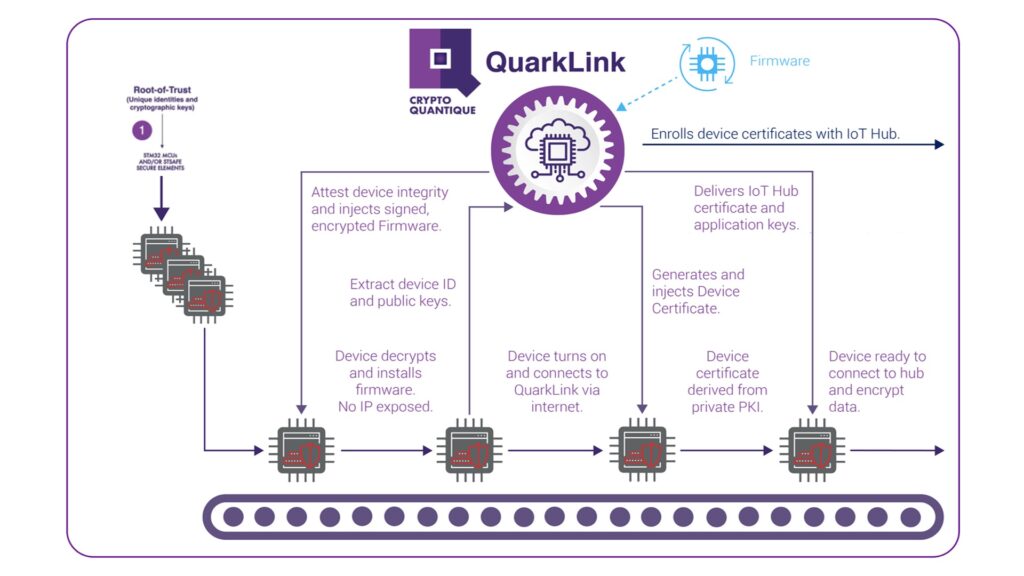
To begin, developers would need a manifest of the Roots of Trust for all devices. It comprises unique IDs and cryptographic keys and is typically extracted during the manufacturing process. Users may keep the manifest on their server, a cloud, or third-party infrastructure that they can import into QuarkLink during configuration. To set up an IoT network, users select predefined security policies and upload the device IDs. Afterward, a device makes an onboarding request to its QuarkLink server over an encrypted TLS channel.
QuarkLink, which has been pre-configured with the security policy, delivers the required security credentials to the IoT device in preparation for connection to the cloud service. The edge system can then talk to the cloud service and upload or download data. As Crypto Quantique explained,
“The most recent Amazon guide to security in the AWS cloud is 27 chapters and 365 pages long. While we applaud the extensive documentation, it highlights the complexity behind large-scale secure IoT networks. QuarkLink simplifies all this by automating it, thus making security accessible to more teams.”